Aport scanis a method for determining which ports on a network are open. As ports on a computer are the place where information is sent and received, port scanning is analogous to knocking on doors to see if someone is home. It is also valuable for testing network security and the strength of the system's firewall. Due to this functionality, it is also a popular reconnaissance tool for attackers seeking a weak point of access to break into a computer.
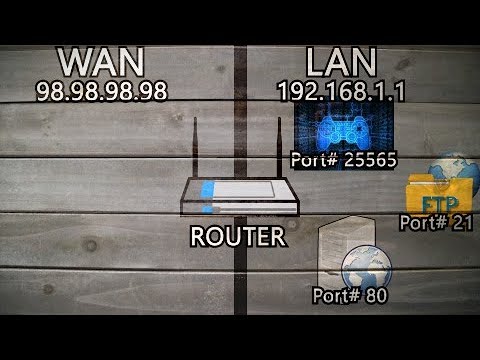
All networks are secured by one firewall on the perimeter of the network, and this firewall is configured to permit HTTP and SMTP traffic to pass through. Other application traffic is forced to use a secured tunnel to pass through the network. Of course, the perimeter firewall is configured to monitor the traffic, and a log is kept for analysis. Internal network is built using Ethernet segments to reflect the infrastructure of the organization. IP network segments are then superimposed on the Ethernet segments. Each IP network segment is secured from each other by a firewall.
Each of the IP segments is connected to the layer-3 switch, thus further protecting each IP segment from an external attack. The IP traffics from the layer-3 switch are directed to pass through a Demilitarized ZONE before it enters the perimeter router. The nodes in the DMZ are DNS, SMTP, and HTTP servers, which are permitted for both inbound and outbound traffic. The attacker would scan the ports on the perimeter firewall and look for open ports on the firewall.
The firewall would have the ports such as 80 and 25 (well-known) open for Web and email services. The goal of the attacker is to find which ports in "listen," "wait," or "closed" state. Nmap includes an advanced port scan option that is used to scan firewalls to determine their connection state and rulesets. The TCP ACK scan (-sA) creates and sends a packet to the target with only the ACK flag set.
Unfiltered systems will respond with a RST packet for both open and closed ports. If an ICMP error message or no response is received, the port is considered filtered by a firewall. These cybercriminals often use port scanning as a preliminary step when targeting networks. They use the port scan to scope out the security levels of various organizations and determine who has a strong firewall and who may have a vulnerable server or network.
The next step is to sweep the target network to find live nodes by sending ping packets and waiting for response from the target nodes. ICMP messages can be blocked, so an alternative is to send a TCP or UDP packet to a port such as 80 that is frequently open, and live machines will send a SYN-ACK packet in response. Thus, we can learn addresses for the target networks' DNS servers, Web servers, and email servers. The GFI Languard NSS software has a utility "whois" that easily allows discovering all the information regarding a domain name registered to a corporate network. DNS Zone transfers refer to learning about the servers and their IP addresses from zone files.
Some malicious software acts as a service, waiting for connections from a remote attacker in order to give them information or control over the machine. Scanning tools used by both attackers and security professionals allow an automated detection of open ports. Many network-based IDS/IPS solutions, and even workstation-based endpoint security solutions can detect port scanning. It is worthwhile to investigate port scanning originating from inside the local network, as it often means a compromised device. However, computers running some security solutions can generate false positives.
This is beacause vendors of security solutions feature a port scanner to detect vulnerable devices inside a home network. Firewall configuration involves configuring domain names and Internet Protocol addresses and completing several other actions to keep firewalls secure. Firewall policy configuration is based on network types called "profiles" that can be set up with security rules to prevent cyber attacks.
Another stealthy scan method is the FTP bounce scan (-b). The FTP bounce scan uses the FTP proxy feature on an FTP server to scan a target from the FTP server instead of your system. The FTP proxy feature allows you to log into an FTP server and request a file to be sent to another system. By sending files to a target system and port you can determine whether a port is open or closed. Most FTP servers no longer support this functionality, but some are still available. The FTP bounce scan can be used to bypass firewalls by scanning from an organization's FTP server, which may be on an internal network, or allowed to the internal network by the firewall rules.
Such an attack would make it difficult to trace the attacker's IP address. We have seen cases of DDOS in spite of the proxy servers' setup to protect the networks. The goal behind port and network scanning is to identify the organization of IP addresses, hosts, and ports to properly determine open or vulnerable server locations and diagnose security levels. Both network and port scanning can reveal the presence of security measures in place such as a firewall between the server and the user's device. This knowledge provides you a starting point for figuring out what Internet traffic to permit through the firewall, and what to deny.
The X server in Red Hat Enterprise Linux 7 clients does not provide the X Security extension. Therefore clients cannot request another security layer when connecting to untrusted SSH servers with X11 forwarding. The most applications were not able to run with this extension enabled anyway. By default, the ForwardX11Trusted option in the /etc/ssh/ssh_config file is set to yes, and there is no difference between the ssh -X remote_machine and ssh -Y remote_machine command. Many services under Red Hat Enterprise Linux 7 are network servers. If a network service is running on a machine, then a server application , is listening for connections on one or more network ports.
Each of these servers should be treated as a potential avenue of attack. Businesses can also use the port scanning technique to send packets to specific ports and analyze responses for any potential vulnerability. They can then use tools like IP scanning, network mapper , and Netcat to ensure their network and systems are secure. Ports exist either in allow mode, or deny (closed; blocked) mode.
If your mail server is in a state of readiness to receive SMTP traffic, we call that "listening on port 25." That means port 25 is open. The main reason you interject a firewall between the Internet and your system is to get in the way of outsiders trying to access open ports. The applications on your network's machines can open ports without waiting for your knowledge or permission.
Some, like peer-to-peer file sharing or video conferencing software, open ports with the single-minded obsession of a frenzied border collie. Each of those open ports becomes another potential hole in your security, gullibly accepting whatever is sent to it, unless you take proactive steps to block it. All of the servers related to NIS can be assigned specific ports except for rpc.yppasswdd — the daemon that allows users to change their login passwords. Assigning ports to the other two NIS server daemons, rpc.ypxfrd and ypserv, allows for the creation of firewall rules to further protect the NIS server daemons from intruders.
Remote Desktop Protocol is a Microsoft proprietary protocol that enables remote connections to other computers, typically over TCP port 3389. It provides network access for a remote user over an encrypted channel. Network administrators use RDP to diagnose issues, login to servers, and to perform other remote actions. Remote users use RDP to log into the organization's network to access email and files. Using PureVPN for forwarding ports is safe because you are building a secure internet connection between two devices with an added security layer. Plus, you can encrypt internet traffic with a VPN connection on your network, and hackers won't easily penetrate the devices.
Also, you can install games and torrents faster with a VPN connection as they offer P2P servers. Whether you have heard about port forwarding or not, we will try to answer this question in simpler words. Port Forwarding allows computers over the internet to connect to a computer or server within a private home network.
This makes your computer accessible to another computer through your network, which is being used to filter traffic to multiple devices on your network. But through port forwarding, you specify that your PC gets traffic to certain ports of your choosing, and your Xbox gets traffic to other ports, and the list goes on. Nmap has two other less used port scanning command-line options that provide valuable information.
The --traceroute command-line option is performed after the scan and works with all scan types except the TCP connect scan (-sT ) and idle scan (-sI ). It uses Nmap's own traceroute algorithm and timing characteristics to determine the mostly likely port and protocol to reach the target. The --reason command-line option shows more detail about the responses from the target host, including the type of packet that was received in response to the probe.
This option is also automatically enabled by the nmap debug (-d ) command-line option. If Nmap receives an ICMP unreachable error it will report the port as filtered. These advanced port scanning options are stealthy and may bypass firewalls and other security controls. However, most host- and network-based intrusion detection systems will detect this type of scan activity. Keep in mind that OSes that don't follow the TCP RFC may send misleading responses.
A port scanner such as Nmap is capable of a wider variety of TCP scans that are harder to detect. Nmap allows an option for a TCP SYN stealth scan in which the third message is not an ACK but a FIN that forces the TCP connection to be closed before fully opening. This half-open connection is not logged at the target, but may be noticed by routers or firewalls that record the original SYN packet.
The purpose of IP Masquerading is to allow machines with private, non-routable IP addresses on your network to access the Internet through the machine doing the masquerading. Traffic from your private network destined for the Internet must be manipulated for replies to be routable back to the machine that made the request. Linux uses Connection Tracking to keep track of which connections belong to which machines and reroute each return packet accordingly. Traffic leaving your private network is thus "masqueraded" as having originated from your Ubuntu gateway machine. This process is referred to in Microsoft documentation as Internet Connection Sharing. As port scanning is an older technique, it requires security changes and up-to-date threat intelligence because protocols and security tools are evolving daily.
Nmap also allows options that give the attacker more control over the packets sent. The attacker can set the rate at which packets are sent, since changing the timing to space out the packets can help avoid raising the target's suspicions that it is being scanned. If the rate is set too fast, packets can be lost, and incorrect results will be returned.
The attacker can also fragment the packets to avoid intrusion detection systems, many of which only look for the whole suspicious packet to be sent at once. We have already discussed the significance of TCP and UDP port numbers, and the well-known and not so well-known services that run at these ports. Each of these ports is a potential entryway or "hole" into the network.
If a port is open, there is a service listening on it; well-known services have assigned port numbers, such as http on TCP port 80 or telnet on TCP port 23. Port scanning is the process of sending packets to each port on a system to find out which ones are open. You'll most commonly detect scans and sweeps from Script Kiddies or other automated, semi-intelligent attacks. More experienced Black Hats will scan more slowly, generally slow enough to avoid being detected by a firewall. This technique of sending port scanning packets infrequently over a long period of time is known as a slow scan. Is used to determine what ports a system may be listening on.
This will help an attacker to determine what services may be running on the system. Some port scanners scan through ports in numeric order; some use a random order. There are many different methods used for port scanning, including SYN scanning, ACK scanning, and FIN scanning. Any idea why this port is still open even with a firewall? Different firewalls may choose differently to leaving Windows NetBIOS file and printer sharing open or closed with their default settings. So, just installing a firewall doesn't instantly protect you.
The firewall may need some help from you to determine what you want to be protected from! Therefore, you may need to examine the software's configuration settings to determine how to close external access to the dangerous NetBIOS ports 137, 138, and 139. The NAT router reformats the outgoing data packet so that it appears to originate from IT, instead of the actual originating machine, and sends it on its way. Then the data returns the process is reversed and the data packet is sent to the originating machine on the private network. Thus, when viewed from the perspective of the external public Internet, ALL of the machines behind the NAT router appear to be a single machine with that one IP address. Though I trust you, I figure that anyone else can see anything that you can.
The accessibility of your machine's IP address does not, in and of itself, represent any real security risk. In order for you to use the Internet at all, information must be able to find its way back to your computer. This requires a two-way path between your computer and remote machines. Your machine's unique IP address is the way data finds its way back to you. It's true that this necessarily creates some degree of security vulnerability, but only as much as is absolutely required for any sort of "connection" to remote resources on the Internet.
How do I protect open ports The best thing to do is to be concerned and responsible about your machine's security. Follow the steps outlined on this site and keep an eye on the security-related software I develop in the future. Finding open ports is typically the overall goal of port scanning and a victory for a cybercriminal looking for an attack avenue. The challenge for IT administrators is trying to barricade open ports by installing firewalls to protect them without limiting access for legitimate users. Cyber criminals don't limit their attacks to web applications, so detection systems shouldn't either. Cyber threat actors use misconfigured RDP ports that are open to the Internet to gain network access.
This popular attack vector allows CTAs to maintain a low profile since they are utilizing a legitimate network service and provides them with the same functionality as any other remote user. CTAs use tools, such as the Shodan search engine, to scan the Internet for open RDP ports and then use brute force password techniques to access vulnerable networks. Compromised RDP credentials are also widely available for sale on dark web marketplaces.
Port forwarding allows external computers to connect to your computer within a private network. This does sound secure because you are configuring the router and feeding it a specific port number. Port forwarding a security camera or computer is also safe but has low reliability. Your computer is safe from external threats while port forwarding if you are using Windows Vista, Windows 7, 8, or 10.























No comments:
Post a Comment
Note: Only a member of this blog may post a comment.